Security Priority One
What we are familiar and often used HTTPs is SSL secure sockets layer/TLS. It needs a public key. First is the handshake protocol where shared handshake public key, then the record layers encrypt. Protect files on disk use symmetric encryption.
Digital cash anonymous; Zero knowledge proof of knowledge do have a solution to the puzzle
History David kahn book.
symmetric ciphers caesar Cipher no key, shift by 3, to break a substitution cipher use the frequency of English letters
Vigener cipher in 16th century, modular 26
Rotor machines rotate and produce a key, the enigma machine by nazi is the most famous
Data Encryption Standard in 1974
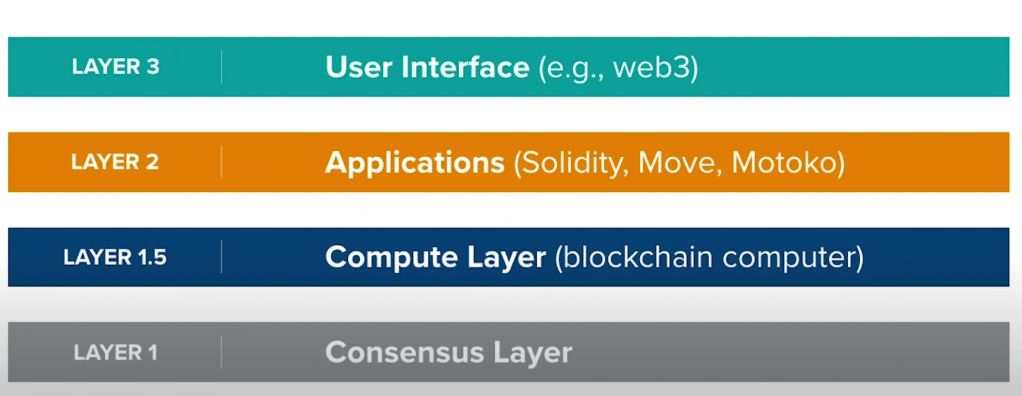
Blockchain is huge development on cryptography, depicted in 4 layers as follows: consensus, compute, application(solidity, move motoko language programing) and top layer is the user interface web 3.0.
There are a great deal of knowledge contained the following content:
************************TIME STAMP***************************************
INTRODUCTION 0:00:00 Course Overview 0:10:34 what is Cryptography 0:26:26 History of Cryptography 0:45:16 Discrete Probability (Crash Course) ( part 1 ) 1:03:23 Discrete Probability (crash Course) (part 2) STREAM CIPHERS 1:17:13 information theoretic security and the one time pad 1:35:46 Stream Ciphers and pseudo random generators 1:55:34 Attacks on stream ciphers and the one time pad 2:18:48 Real-world stream ciphers 2:38:26 PRG Security Definitions 3:03:20 Semantic Security 3:18:51 Stream Ciphers are semantically Secure (optional) BLOCK CIPHERS 3:29:46 skip this lecture (repeated) 4:02:25 What are block ciphers 4:19:10 The Data Encryption Standard 4:41:09 Exhaustive Search Attacks 5:00:51 More attacks on block ciphers 5:16:54 The AES block cipher 5:30:28 Block ciphers from PRGs USING BLOCK CIPHERS 5:42:12 Review- PRPs and PRFs 5:53:43 Modes of operation- one time key 6:00:57 Security of many-time key 6:23:47 Modes of operation- many time key(CBC) 6:40:00 Modes of operation- many time key(CTR) MESSAGE INTEGRITY 6:49:20 Message Authentication Codes 7:04:36 MACs Based on PRFs 7:14:34 CBC-MAC and NMAC 7:34:15 MAC Padding 7:42:55 PMAC and the Carter-wegman MAC COLLISION RESISTANCE 7:58:21 Introduction 8:09:15 Generic birthday attack
The second part is here. *********TIME STAMP*************** COLLISION RESISTANCE 0:06:21 The Merkle-Damgard Paradigm 0:17:54 Construction Compression functions 0:26:03 HMAC 0:33:07 Timing attacks on Mac Verification AUTHENTICATED ENCRYPTION 0:41:36 Active attacks on CPA-secure encryption 0:54:30 Definitions 0:59:44 Chosen ciphertext Attacks 1:11:49 Constructions from ciphers and MACs 1:32:07 Case Study 1:49:46 CBC padding attacks 2:03:52 Attacking non-atomic decryption ODDS AND ENDS 2:13:42 Key Derivation 2:27:17 Deterministi Encryption 2:41:50 Deterministic Encryption-SIV and wide PRP 3:02:19 Tweakable encryption 3:16:44 Format Preserving encryption BASIC KEY EXCHANGE 3:28:58 Trusted 3rd Parties 3:40:10 Merkle Puzzles 3:51:28 The Diffie-Hellman Protocol 4:10:29 Public-key encryption INTRODUCTION TO NUMBER THEORY 4:21:25 Notation 4:35:41 Fermat and Euler 4:53:46 Modular e-‘th roots 5:10:54 Arithmetic algorithms 5:23:29 Intractable problems PUBLIC KEY ENCRYPTION FROM TRAPDOOR PERMUTATIONS 5:42:09 Definitions and Security 5:57:49 Constructions 6:08:14 The RSA trapdoor permutations 6:25:48 PKCS1 6:46:56 Is RSA a one-way function 7:03:31 RSA in practice PUBLIC KEY ENCRYPTION FROM DIFFIE-HELLMAN 7:17:26 The ElGamal Public-key System 7:36:55 ElGamal Security 7:50:07 ElGamal Variants with Better Security 8:00:28 A Unifying Theme 8:12:12 Farewell (for now)
The same professor Dan Boneh also talks about Blockchain technology in cryptography.